Domain fronting is a technique often used to bypass censorship, but it turns out it’s also pretty handy for hiding C2 traffic.
Rather than explain what domain fronting is or how it works I’d recommend reading these two links:
Before getting into it, there are a few prerequisites that will need to be met for this to work:
- You’ll need an Amazon account. This demo uses the CloudFront service, it will work fine with Google too but that isn’t covered in this post.
- A Windows machine with a real world IP address
- A domain name
- A legitimate SSL certificate for the above mentioned domain name (Let’s Encrypt is fine)
Before using this technique for anything sensitive, be sure you fully understand how CloudFront works and the implications of using it to transmit sensitive data.
First things first, you’ll need to generate or acquire legitimate SSL certs for your domain. I’ll leave this as an exercise to the reader but you’ll need both the certificate and the private key on your Windows machine.
Once both the files are on your Windows machine you’ll need to convert them to a file Windows understands and install them.
To convert them you’ll need openSSL, precompiled Windows binaries can be found here.
Unzip the archive, drop the cert and private key in the same directory before running the below command:
openssl.exe pkcs12 -inkey privkey.pem -in cert.pem -export -out priv.pfx
Next up you need to install the cert, just double click the newly generated priv.pfx and Windows should launch a wizard. Make sure to import the cert to the Store Location of “Local Machine” rather than the current user. Other than that, the defaults are fine so just keep hitting next.
Now we need to ensure the cert is used:
#This will list the thumbprints of any certs you've got installed
#Copy the thumbprint of the cert you're going to be using
dir cert:\localmachine\my
#Delete any other certs which may be in use
netsh http delete sslcert ipport=0.0.0.0:443
#Install the new cert
netsh http add sslcert ipport=0.0.0.0:443 certhash=[Thumbprint here] 'appid={00112233-4455-6677-8899-AABBCCDDEEFF}'
The new cert should be installed and ready to go now.
The next thing that needs setting up is CloudFront.
Once logged in, begin the process of creating a new web distribution.
Set the Origin Domain Name as the domain you’ve got your C2 server set up with and follow the settings as below:
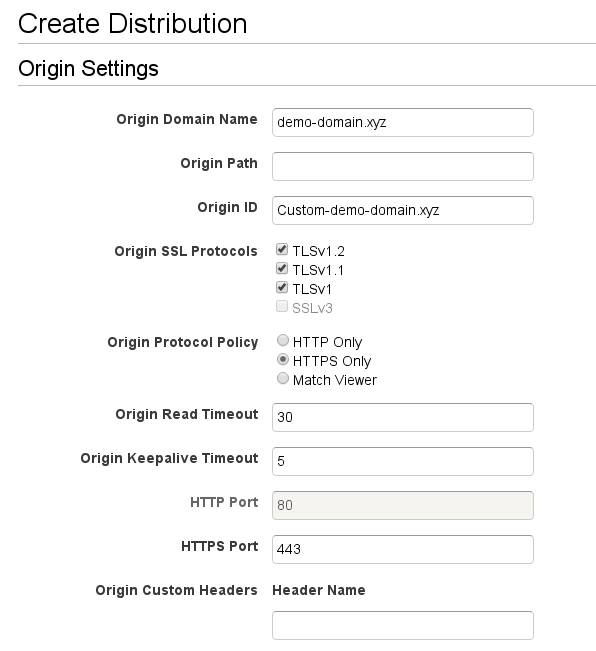
The main things to alter are the “Allowed HTTP Methods”, “Forward Headers”, “Forward Cookies” and “Query String Forwarding and Caching” 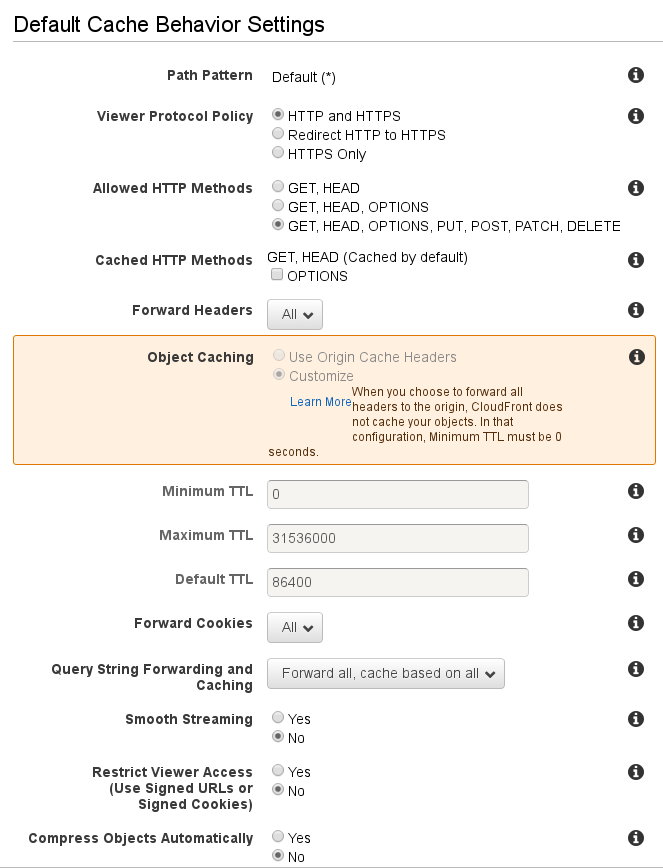
Once you’re done it will take ~ 15 minutes for the distribution to be fully deployed.
Be sure to grab the CloudFront domain name, this will need be used as the HTTP Host header for your implants.
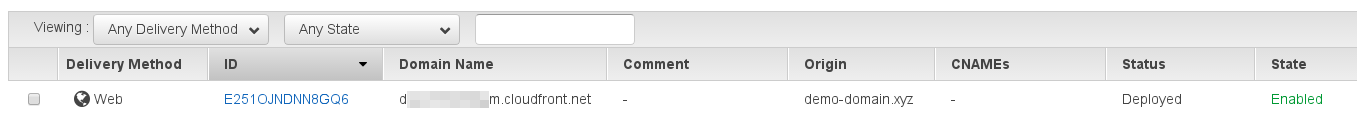
Once it’s deployed you’re pretty much ready to roll. All you need to do now is set up PoshC2 and it’s time to start causing mayhem and hopefully avoiding the blue team whilst you’re at it.
Make sure you’ve got the latest version of PoshC2 installed and follow the below to get PoshC2 configured with your CloundFront domain name:
#Start the C2 server
[1] Enter the IP address or Hostname of the Posh C2 server (External address if using NAT) [REDACTED]: d0.awsstatic.com
[2] Do you want to use HTTPS? [Yes]: Yes
[2a] Do you want PoshC2 to create a new self-signed SSL certificate, PSv4 required? [Yes]: No
[2b] Do you want to use domain fronting, if so specify the host header?: REDACTED.cloudfront.net
[3] Enter a new folder name for this project [PoshC2-2017-10-05-1014]: DomFrontDemo
[4] Enter the default becaon time in seconds of the Posh C2 server (10% jitter is always applied) [5]:30
[5] Enter the auto Kill Date of the implants in this format dd/MMM/yyyy [24/May/2017]:
[6] Enter the HTTP port you want to use, 80/443 is highly preferable for proxying [443]:
[7] Do you want to enable sound? [Yes]: No
That’s it. You should be up and running.
After running a payload on a victim VM, I see the below traffic in Wireshark.
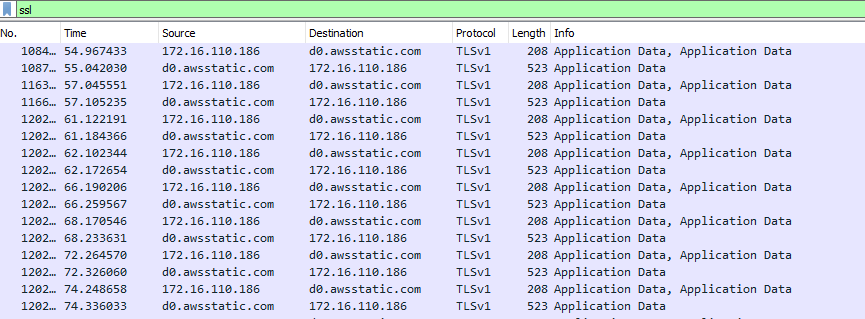
As you can see, traffic is going to and from https://d0.awsstatic.com and will be using a legitimate, CA signed SSL cert owned by Amazon.
This should blend in nicely with standard HTTPS traffic and should hopefully fly under the radar.